Hydra is a brute force online password cracking tool, a very fast network logon cracker that supports many different services. Hydra is a command line tool, however, it has a GUI version called xhydra.
Hydra has the ability to brute force the following protocols: Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-POST, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD, HTTPS-POST, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MYSQL, NCP, NNTP, Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, RDP, Rexec, Rlogin, Rsh, RTSP, SAP/R3, SIP, SMB, SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
You can check the official Kali Linux Hydra tool page for more information - https://en.kali.tools/?p=220
Installation
- You can download it from GitHub - https://github.com/vanhauser-thc/thc-hydra. Check HOW TO COMPILE.
- Or you can use the apt command - sudo apt install hydra-gtk.
Usage
Commands
- We need to brutefore FTP protocol. We have the information that the username is hackhunt and we need to find the password.
- For SSH. Suppose in this case we don't know the username or password and need to brute force both.
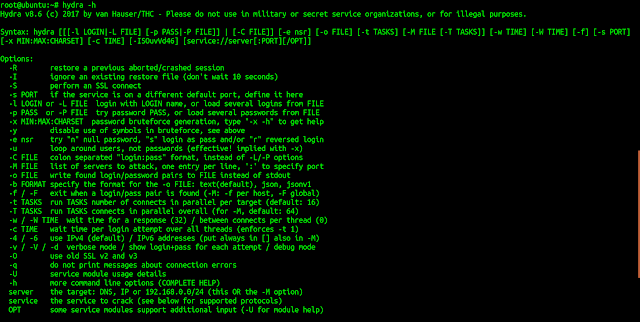
Important Flags to know:
| Flag | Description |
|---|---|
| -l | specify a single username |
| -L | specify wordlist for usernames |
| -p | specify a single password |
| -P | specify wordlist for passwords |
| -t | specifies the number of threads to use |
| -s | specify the port, which can be used when the service is not running on the default port. |
| -V | Verbose output for every attempt |


%20Cover.jpg)
%20Cover.jpg)



No comments:
Post a Comment