Let's dig in deep with the Intrusion Detection System (IDS) and Firewall
Invasion techniques. Network obstructions such as firewalls can make
mapping a network difficult. In addition to restricting network activity,
companies are increasingly monitoring traffic with intrusion detection systems
(IDS).
All of the major IDSs ship with rules designed to detect Nmap scans because
scans are sometimes a precursor to attacks. Attackers with patience, skill,
and the help of certain Nmap options can usually pass by IDSs undetected.
Meanwhile, administrators must cope with large numbers of false-positive
results where innocent activity is misdiagnosed and alerted on or blocked.
First things first, you can use the help command for Nmap by
typing nmap -h.
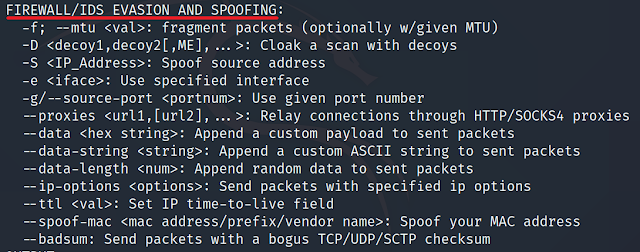
- Tells the requested scan including ping scans to use tiny fragmented IP packets.
- The idea is to split up the TCP header over several packets to make it harder for packet filters, and intrusion detection systems to detect what you are doing.
- Nmap splits the packets into eight bytes or less after the IP header. Specify -f again to use 16 bytes per fragment.
- Using the specified MTU (-mtu <value>)
- You can specify your own offset size with this option.
- Don't also specify -f if you use --mtu.
- The offset must be a multiple of eight.
Cloak a scan with decoy (-D <IPs>)
- Cause confusion as to where the scan came from.
- Packets originate from your system but have a different or spoofed source IP Address.
- It is very noisy in terms of detection as multiple IPs try to scan the network.
- Separate each decoy host with commas, and you can optionally use ME as one of the decoys to represent the position of your real IP address.
nmap <target> -D <FAKE_IP>,<FAKE_IP>,<FAKE_IP>,ME,<FAKE_IP>
Spoof source address (-s <IP>)
- If Nmap is unable to get your IP address use this option to specify the IP address.
- Another possible use of this flag is to spoof the scan to make the targets think that someone else is scanning them.
- The -e (use this option to define interface) option and -Pn are generally required for this sort of usage.
- Usually, you won't receive reply packets back they will be addressed to the IP you are spoofing Not useful in generating reports.
Spoof source port number (-g/--source-port <port_number>)
- One surprisingly common misconfiguration is to trust traffic based only on the source port number. As a result, this option can be used to exploit weaknesses and bypass network filters and firewalls.
- Common ports which are considered trusted are:
- DNS - 53/TCP/UDP
- FTP - 20/TCP
- Kerberos - 88/TCP/UDP
- DHCP - 67/UDP
Relay TCP connections through a chain of Proxies (--proxies)
- Can hide the true source of a scan.
- Can evade firewall restrictions.
- This only supports HTTP and SOCKS4.
- This option is Not Recommended right now as it is still under development and has no effect on the ping, port scanning, and OS discovery phases of a scan.
Append custom string to sent packets (--data-string <string>)
- Add a regular string as a payload in sent packets.
- Note that some characters may depend on your system's locale and the receiver may not see the same information.
- Enclose the string in double quotes and escape any special characters from the shell.
- Example:
nmap <target> --data-string "Security scan by Hack Hunt"
Append random data to sent packets (--data-length <number>)
- Append the given number of random bytes to most of the packets it sends, and not use any protocol-specific payloads.
- OS Detection (-O) is not affected. Furthermore, it slows down the scan.
Randomize Target hosts order (--randomize-hosts)
- This can make the scans less obvious to various network monitoring systems, especially when you combine them with slow-timing options.
- Nmap shuffles each group of up to 16384 hosts before it scans them.
Spoof MAC Address (--spoof-mac <MAC address, prefix, or vendor name>)
- This option only affects raw packet scans such as SYN scans or OS detection.
- Valid --spoof-mac argument examples are Apple, 0, 01:02:03:04:05:06, deadbeefcafe, 0020F2, and Cisco.
- Not Recommended, instead change the MAC Address manually or use a tool.
We hope this helps. If you have any suggestions or doubts you can add a comment and
we will reply as soon as possible.


%20Cover.jpg)
%20Cover.jpg)



No comments:
Post a Comment