Administrators often use port scanning techniques to verify the security
policies of their networks, whereas attackers use them to identify open ports
and running services on a host with the intent of compromising the network.
Furthermore, users occasionally leave needless open ports on their systems
without realising it. Such open ports are exploited by an attacker to launch
assaults.
This article is divided into two articles. Continue reading
Part 1.
UDP Scanning (-sU)
The UDP scan is less informal concerning an open port because there is no
overhead of a TCP handshake. This scan performed exceptionally well on Windows-based hardware. Sending a
packet using the UDP protocol can be trickier than using TCP scanning since
you can't tell if a host is filtered, dead, or alive.
If you send a UDP packet to a port without an application bound to it, the
IP stack will return an ICMP port unreachable packet. if any port returns an
ICMP error, it will be closed, leaving the ports that did not answer if they
are open or filtered through the firewall.
The UDP scan provides port information Only. It also requires privileged
access; hence, this scan option is only available on systems with the
appropriate user permissions.
In nmap, the -sU option is used to perform a UDP
scan.
SCTP Scanning
SCTP INIT Scanning (-sY)
SCTP stands for String Control Transmission Protocol. It is a relatively new alternative to the TCP and UDP protocols, combining
most characteristics of TCP and UDP. SCTP association comprises a four-way
handshake method. The client initiates the connection with INIT, gets
back INIT-ACK, then sends COOKIE-ECHO, and gets back
COOKIE-ACK. Transmission of these four packets completes the SCTP
Association.
Similar to TCP SYN, this scan is likewise relatively undetectable and stealthy
because it leaves the connection half open because it is unable to finish SCTP
associations. Attackers send INIT chunks to the target host. If the port
is listening or open, it sends an acknowledgement as an INIT+ACK chunk.
If the port is not listening or inactive, it sends an acknowledgement
as an ABORT chunk.
The port is filtered if, after several transmissions, there is no response or
if an ICMP unreachable exception is returned. In nmap,
the -sY option is used to perform this scan.
SCTP COOKIE ECHO Scanning (-sZ)
It is a more advanced type of scan. Only a good IDS will be able to detect the
SCTP COOKIE ECHO chunk. It takes advantage of the fact that SCTP
implementations should silently drop packets containing COOKIE ECHO chunks on
open ports, but send an ABORT if the port is closed. It displays the output as open|filtered in all scenarios and
is unable to distinguish between open and filtered ports.
In nmap, the -sZ option is used to perform this
scan.
SSDP Scanning
Simple Service Discovery Protocol (SSDP) is a network protocol that generally
controls communication for the Universal Plug and Play (UPnP)
feature. The SSDP service will respond to a query sent over IPv4 or IPv6
broadcast addresses. Details regarding the related UPnP feature are included in this response.
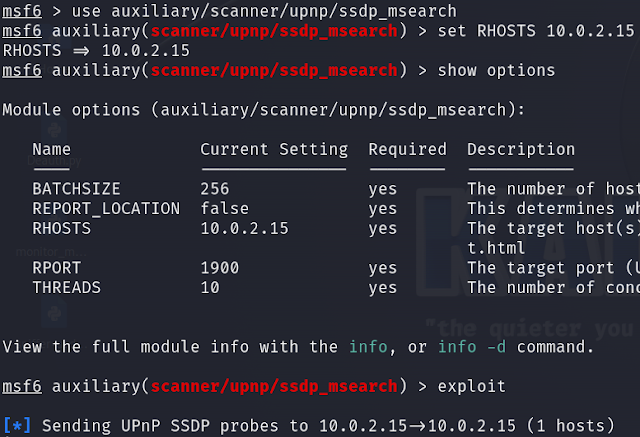
The UPnP SSDP M-SEARCH information discovery tool can be used by the
attacker to determine if the device is susceptible to UPnP exploits. This
can be achieved using the MSFCONSOLE tool. Use
ssdp_msearch, set the RHOSTS to the target IP
address and enter exploit.
List Scanning
This type of scan simply generates and prints a list of IPs/Names without
actually pinging them. By default, a reverse DNS resolution is still carried
out on each host by Nmap to learn their names. In nmap, the
-sL option is used to perform this type of scan.
IPv6 Scanning
To allow for more levels of address hierarchy, IPv6 expands the capacity of an
IP address from 32 bits to 128 bits. Attackers need to harvest IPv6
addresses from network traffic, recorded logs, or Received from: (header lines
in archived emails). In nmap, the -6 option is used to scan for IPv6
addresses.
Service Detection
All that version detection techniques do is look up TCP and UDP ports. Each
port has a designated service, and each service has a version. An attacker can determine which attacks the target system is vulnerable to
by getting precise service version numbers.
For instance, an attacker can quickly launch a WannaCry ransomware attack using Metasploit's eternalblue and doublepulsar backdoor combination if they identify the SMBv1 protocol as a running service on the target Windows PC.
For instance, an attacker can quickly launch a WannaCry ransomware attack using Metasploit's eternalblue and doublepulsar backdoor combination if they identify the SMBv1 protocol as a running service on the target Windows PC.
In nmap, the -sV option is used to detect service versions.
You might be interested in,
- Port Scanning Techniques - Part 1
- Nmap - Port Scanning Techniques (Summary)
- Port Scanning Countermeasures
- Phases of Hacking
- OS Discovery and Countermeasures
- Host Discovery Techniques via Scanning
- Working of TCP 3-Way Handshake
- Introduction to Scanning - Second Step to Hacking
We hope this helps. If you have any suggestions or doubts you can add a
comment and we will reply as soon as possible.


%20Cover.jpg)
%20Cover.jpg)



No comments:
Post a Comment