ParamSpider is a tool which is written in python that is able to find the
parameters which are available on a particular domain or the URL after
crawling, this tool is helpful for Web Application Penetration Testers as well
as Bug Hunters & Security Researchers for finding parameters that might be
vulnerable to test the particular payloads which will help to find various
types of vulnerabilities. It also finds parameters from target subdomains and
has support for URLs with specific extensions. ParamSpider mines the parameters from web archives without interacting with
the victim host.
-
The GitHub repository can be cloned using the command -
git clone https://github.com/devanshbatham/ParamSpider.git.
-
Once the repository has been cloned. Re-direct to the folder using the cd
command. Before starting the tool we need to install a few python packages.
This can be done using the command
pip3 install -r requirements.txt.

|
|
Installing required Python Packages
|
It is always a good practice to
check the help command to know more about the tool and how to use it. This can
be done using the command
python3 paramspider.py --help
-
A few of the important flags which can be used during your enumeration
process are:
- -d <doamin_name>: Specify the target domain.
-
-o <file_name>: Save the output to a file with the specified
name. The default is domain.txt.
-
-q: Quiet Mode. The output will be not shown on the screen i.e. no
verbose mode.
-
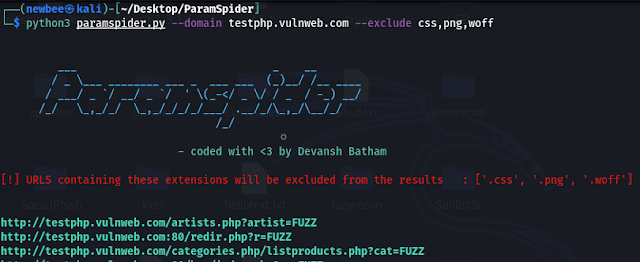
-e: Exclude certain types of URLs which are generally false alarms
as a parameter for a website. For example .css

|
|
Example of the command using Quit Mode
|
|
|
Example of the command without the Quit Mode
|
-
The output is saved to the file as mentioned. To view the output
the cat command can be used.

|
| Saved Output |
ParamSpider can find the parameters which
are hiding deep in a website. These parameters are very useful because they
can be tested with bugs such as XSS, SQL injection, SSRF, or open redirect
easily.
We hope this helps. If any suggestions or doubts you can add a comment and
we will reply as soon as possible.






%20Cover.jpg)
%20Cover.jpg)



No comments:
Post a Comment